DNS Sinkhole: Its role in Cyber security
People are very comfortable clicking on website links these days. This trend is a blessing for the criminals creating and spreading a ludicrous number of malicious URLs. Infected links can automatically download malware to your device or lead to spoofed websites that will trick you into divulging sensitive information. This is obviously a threat to organizations whose ability to maintain data security contributes largely to their success. DNS sinkhole is one way to cut off malicious URLs in a way that focuses on the entire network rather than individual endpoints.
What is a DNS Sinkhole?
DNS sinkhole is a cyber security technique that counteracts and neutralizes malicious online activities. It operates by intercepting and redirecting Domain Name System (DNS) requests, which are essential for translating human-readable domain names into IP addresses. Think about your home with locks on the doors to keep it safe. Similarly, computers and networks need protection from bad things happening online. That’s where the DNS sinkhole comes in. It’s like a digital lock that stops bad stuff from getting into your network.
When you want to visit a website, your browser asks a DNS server to find the address of that website. A DNS sinkhole is like a guard at the entrance. It checks if the website you’re trying to visit is safe. If it’s not safe, the guard sends you to a different address so you don’t accidentally end up in a dangerous place.
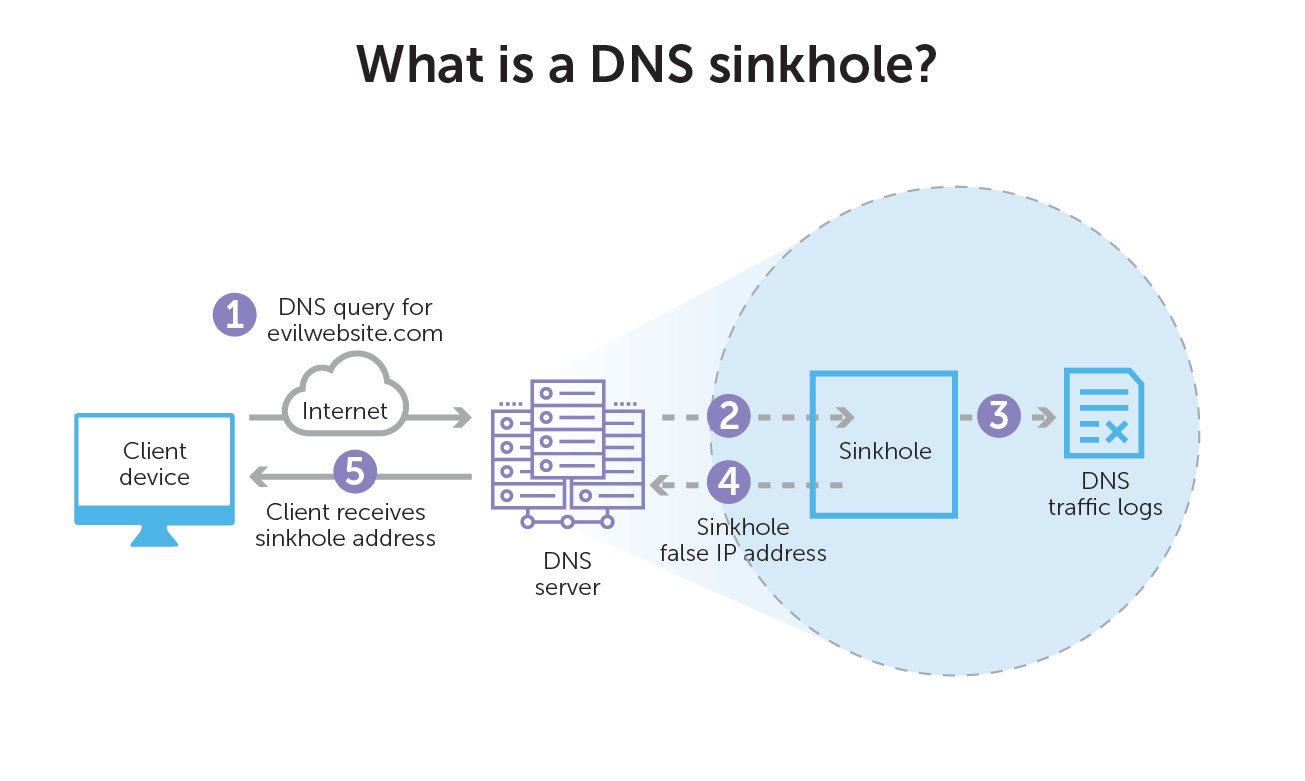
How does it operate?
The operation of a DNS sinkhole is relatively straightforward yet powerful in its cybersecurity implications. Here’s a step-by-step breakdown:
- Interception: When a request is made from within a network to access a domain, the DNS sinkhole can intercept this request if the domain is recognized as malicious.
- Redirection: Rather than allowing the request to proceed to the potentially harmful domain, the DNS sinkhole redirects it. This redirection might lead to a benign IP address, essentially a dead end, or to a server controlled by the network administrators for further analysis.
- Protection: As a result, any device within the protected network is inhibited from establishing connections with sites known for hosting malware, phishing scams, or other cyber threats, thereby maintaining the network’s integrity and security.
Choices for implementing a DNS Sinkhole
Administrators have three options for adding a DNS sinkhole to their request chains.
- Trusting a third-party service as a DNS forwarder
- Setting up and configuring a private DNS server
- Using a firewall with a sinkhole feature
The easiest method is outsourcing a third-party service with sinkhole capabilities. Administrators lose some customization options, but it will take the shortest time to get set up and protected. There are also no maintenance costs, and you don’t have to curate a personal list of dangerous domains.
However, if control is vital to your operations, setting up your own DNS server isn’t the worst choice. Someone knowledgeable must be ready to address problems and analyze the logs for security research.
Rather than integrating a new service into your operations, you might be able to pull similar effects from your existing firewall. You can use the support options of the firewall to address problems and configure a database of domains to redirect. The risk with this option is that if the firewall goes down, the sinkhole goes down with it, whereas a separate service would act as a redundant security measure.
Limitations of DNS sinkhole
There are several limitations related to DNS sinkholes.
To block malware or its traffic by using a DNS sinkhole, it is required by the malware to use the organization’s DNS server itself. Malware with its own hardcoded DNS server and IP address cannot be detected by the DNS sinkhole mechanism. But this drawback can be mitigated by using perimeter firewalls configured to block all other outbound DNS queries rather than the organization’s DNS servers.
A DNS sinkhole cannot prevent malware from being executed and also being spread to other computers. Also, by using a DNS sinkhole, malware cannot be removed from an infected machine.
A DNS sinkhole will be put in with the indicators of the malware, and these indicators should be analyzed beforehand. Also, the malicious IP information gathered from open sources that are to be given into the DNS sinkhole may contain false positives. The sources may contain a URL that is not malicious, and hence it will result in an unwanted restriction to legitimate websites.
A DNS sinkhole should be isolated from the external network so that the attacker cannot be informed of the fact that their C&C traffic has been mitigated. Otherwise, it results in a reverse effect where attackers may manipulate the entries in the DNS sinkhole and use them for malicious purposes.
DNS records should be implemented with time-to-live (TTL) settings with short values, or it may result in users caching the old data for a longer period.

Conclusion
A DNS sinkhole is a clever way to leverage the existing DNS protocol to extend protective capabilities. Even if malware does become active on systems in your network, this strategy often prevents the malware from performing its malicious goal by preventing it from beaconing out to a command and control server.
DNS sinkholes empower administrators to pre-emptively block traffic to malicious domains by forwarding the traffic to a sinkhole instead of the harmful destination. This offers a leg up on malicious software and acts as an additional layer of defense for the network.