Hardware Firewall: Everything you need to know
A firewall is a cybersecurity tool widely used to secure computer networks from unauthorized users. A firewall is used for information security and can be a hardware firewall or a software firewall, or a combination of both, depending on the requirements of the client.
What is a hardware firewall?
A hardware firewall, otherwise known as a physical firewall, is an appliance that establishes a network boundary. It’s a set of appliances or devices that are used in defending the computer network. A hardware firewall is a device that connects a computer network to an external internet and acts as a barrier that protects the computer network from hackers or users that are not authorized to access the network.
A hardware firewall aids the cybersecurity of the computer network by filtering the traffic that gets through, which was established based on security policy, users profile, and rules. The boundary set prevents unauthorized access, inspects all inbound and outbound network traffic, and manifests controls and security policies.

Who Needs A Hardware Firewall?
The hardware firewall is being widely adopted in a range of different scenarios including:
- In enterprises that require higher security for a network of computers.
- Enterprises need total security for their operational areas, without risk of breach.
- Those where they have the human resources needed to maintain the firewall and equipment.
- Businesses require reliability and the ability to control their environment.
- Businesses who perform upgrades frequently
How does it work?
A traditional firewall has controls in terms of protecting data from outsiders however, the data or information from the local network may not be secure. A hardware firewall is a security approach that distinguishes between trusted and untrusted networks. A hardware firewall encloses all connections between two networks, allowing all traffic to pass until it meets assertive criteria, or denying all traffic unless and until it fulfills assertive criteria based on security policy decisions made in advance by the security administrator. Traditional firewalls, also known as perimeter firewalls, are security guards that are positioned on the network’s boundary. The hardware firewall imposes a central policy on which firewalls are permitted to enter and exit the network. The aggressive criteria used to determine whether to admit or prohibit traffic vary from one firewall to the next.
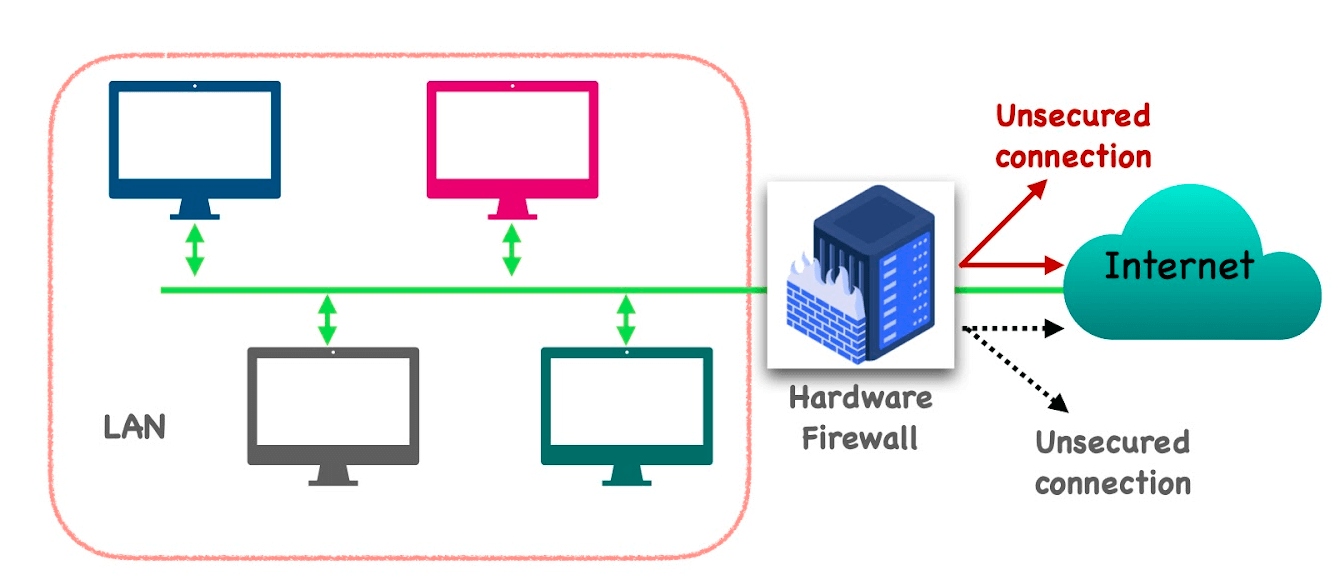
When traffic passes through the hardware firewall, it is assessed using a set of rules based on the kind of traffic, source or destination IP addresses, or port numbers. The hardware firewall may also include complex rule bases that examine and analyze application data to determine whether or not traffic should be allowed to pass through. This point must always be traversed by all traffic entering or exiting the network. The main declension of a firewall is this requirement. A firewall, in essence, inspects all traffic between the two networks and ensures that it complies with all pre-defined prototypes and protocols. A hardware firewall is sent between those networks only if they follow the prettified prototype; otherwise, it is stopped if they do not. A firewall not only helps to prevent the admission of undesired or malicious hosts or users, but it also helps to protect against the following threats:
- Incoming and outgoing traffic are both filtered by a firewall.
- It can also control public access to personal data sources like host applications.
- Address filtering allows firewalls to filter packets based on their source and destination addresses as well as port numbers.
- Protocol filtering is a feature of firewalls that allows them to filter specific types of network traffic. Filtering traffic by packet attribute or state is also possible with firewalls.
- It can be used to keep track of all efforts to gain access to the private network and to raise an alarm if a hostile or unauthorized entrance is detected.
Key Benefits of Hardware Firewalls
Hardware firewalls, deployed as physical appliances, provide several benefits compared to software firewalls, including:
- Consistent Security: Software firewalls installed on different computers can all be configured differently. Unless an organization can implement and enforce a consistent security configuration, software firewalls may be disabled or have varying levels of security. A hardware firewall, on the other hand, provides consistent protection to all devices protected by it.
- Standalone Protection: A software firewall likely runs on the protected computer. This means that it takes up resources that could otherwise be used for other purposes. A hardware firewall runs on its hardware, meaning that increases in traffic volume or security requirements do not impact the performance of the protected machines.
- Simplified Management: With a software firewall, each computer needs to be individually configured, managed, and updated to provide strong protection against cyber threats. A hardware firewall, on the other hand, is a single appliance that protects the entire network. Any updates or configuration changes that are required can be applied once and will instantly apply to all devices protected by the firewall.
- Improved Security: A hardware firewall runs on its dedicated hardware instead of relying on the resources of the computer where it is installed. This can help to protect it against attacks designed to exploit the underlying operating system or the programs running alongside it.
- Centralized Visibility: Running independent software firewalls on each device within an organization’s network means that the security team either lacks complete network visibility or must put in extra effort to aggregate and assimilate information from all of the various devices. A hardware firewall centralizes all network monitoring and logging in a single appliance.

Conclusion
A hardware firewall is a device or set of devices used to protect individual computers or a network of computers from the threat of information or data leakage. It acts by filtering out requests from unauthorized users to access data. Finally, despite all the resources spent and a dedicated team in charge, we still keep hearing about incidents of huge data leakages from major corporates. This can only be prevented by constant vigilance, up-gradation, and monitoring of the systems without any complacency.