Transport Layer – Layer 4 of the OSI Model: What is it?
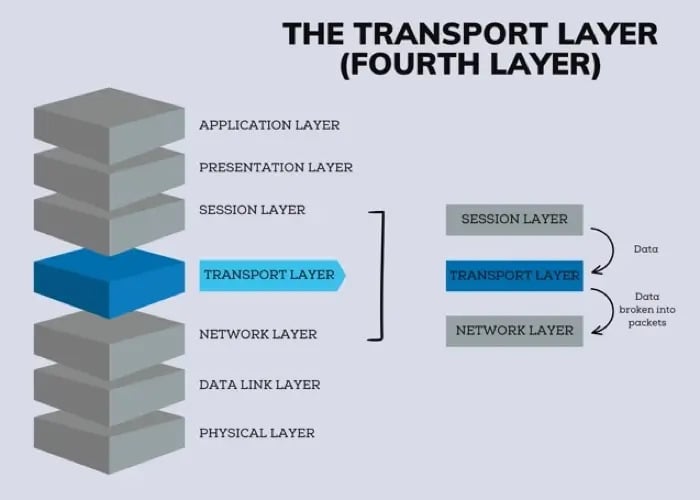
In the OSI suite, there are 7 layers and all layers provide different services. Today we are here with detailed information on one of the layers i.e. transport layer which provides process-to-process communication in the OSI suite. Transport Layer in Computer Networks is an end-to-end layer that is used to deliver messages to a host. In the OSI model, the transport layer is located between the session layer and the network layer.
What is the Transport Layer?
The transport layer is the fourth layer in the open systems interconnection (OSI) network model. The OSI model divides the tasks involved with moving information between networked computers into seven smaller, more manageable task groups. Each of the seven OSI layers is assigned a task or group of tasks.
The transport layer’s tasks include error correction as well as segmenting and desegmenting data before and after it’s transported across the network. This layer is also responsible for flow control and making sure that segmented data is delivered over the network in the correct sequence.
Layer 4 (the transport layer) uses the transmission control protocol (TCP) & user data protocol (UDP) to carry out its tasks.
How does it work?
It takes services from the Application layer and provides services to the Network layer.
- At the sender’s side: The transport layer receives data (message) from the Application layer and then performs Segmentation, divides the actual message into segments, adds the source and destination’s port numbers into the header of the segment, and transfers the message to the Network layer.
- At the receiver’s side: The transport layer receives data from the Network layer, reassembles the segmented data, reads its header, identifies the port number, and forwards the message to the appropriate port in the Application layer.
Transport layer functions
- Connection-oriented communication. Before exchanging data, network devices need a handshake protocol like TCP to establish a secure connection. This method’s disadvantage is that each delivered message requires an acknowledgment, which increases the network burden compared to self-error-correcting packets. Repeated queries delay the network when faulty byte streams or datagrams are transmitted.
- Same order delivery. Assign a sequence number to each packet to guarantee they are delivered in that order. Even while packet drops and device interruptions are the responsibility of the network layer, the transport layer can reshuffle the packets to correct the order.
- Data integrity. Protecting data integrity by checksums. With the checksums in place, you can rest assured that your data will arrive in an uncorrupted form regardless of how far it travels.
- Multiplexing. The transport layer has specific control methods for multiplexing packet streams from unrelated applications or sources over a network. Multiplexing lets computers run numerous internet browsers at once over a network. The OSI service layer handles multiplexing.
- Flow control. Controlling the rate at which information is transmitted.
- Traffic control. The transport layer can recognize the signs of overloaded nodes and decreased throughput and take corrective action.
- Byte orientation. The transport layer can send byte streams instead of packets for applications that prefer them.
Transport layer protocols
In the TCP/IP protocol suite, the two main protocols are the TCP (Transmission Control Protocol) and the (UDP) User Datagram Protocol. Within these protocols, various other protocols are controlled by them. These protocols manage the different applications that communicate over the network. They differ in several ways as described below.
UDP is used when the communication stream does not depend fully on the connection. This means that one end can be connected to the network while the other side is temporarily down. Communication does not have to be in on stream for it to work. This is unreliable transport. Some of the applications that are implemented using UDP include; DNS – Domain Name System which is how devices resolve ip addresses to names, Voice Over IP (VOIP) which is where calls can be made over a network and also streaming video
Transmission Control Protocol (TCP)
For TCP to work, the connection has to be established. This means that both ends of the communication; the sender and recipient must be online for it to work. This means that it uses reliable transport. Some of the applications that are implemented using TCP include; HTTP and HTTPS for websites, E-mail using SMTP and POP, and file transfers using FTP.
Conclusion
- The transport Layer is the fourth layer of the TCP/IP suite which provides process-to-process communication
- Transport Layer provides process-to-process communication, data integrity, flow control, congestion avoidance, multiplexing, and demultiplexing services.
- UDP is a Transport layer protocol that provides connectionless service.
- TCP and SCTP is Transport layer protocol that provides connection-oriented service.