What is a Jump Server?
As network perimeters expand and cyber security challenges grow, implementing jump servers has become a vital strategy for enhancing security in IT infrastructures. These specialized servers manage controlled access to network resources, acting as a secure gateway that shields sensitive internal systems from potential threats. By mitigating the risks associated with direct remote access, jump servers serve as a critical checkpoint, ensuring that only authenticated users can reach essential assets.
What is a Jump Server?
A jump server, also known as a jump host or gateway, is a secured and controlled server that acts as an intermediary between a user’s workstation and other servers or devices within a network, particularly in a demilitarized zone (DMZ). Its primary purpose is to provide a single point of access from which administrative tasks or management functions can be performed on other servers or networked devices, enhancing security by limiting direct access to the internal network.
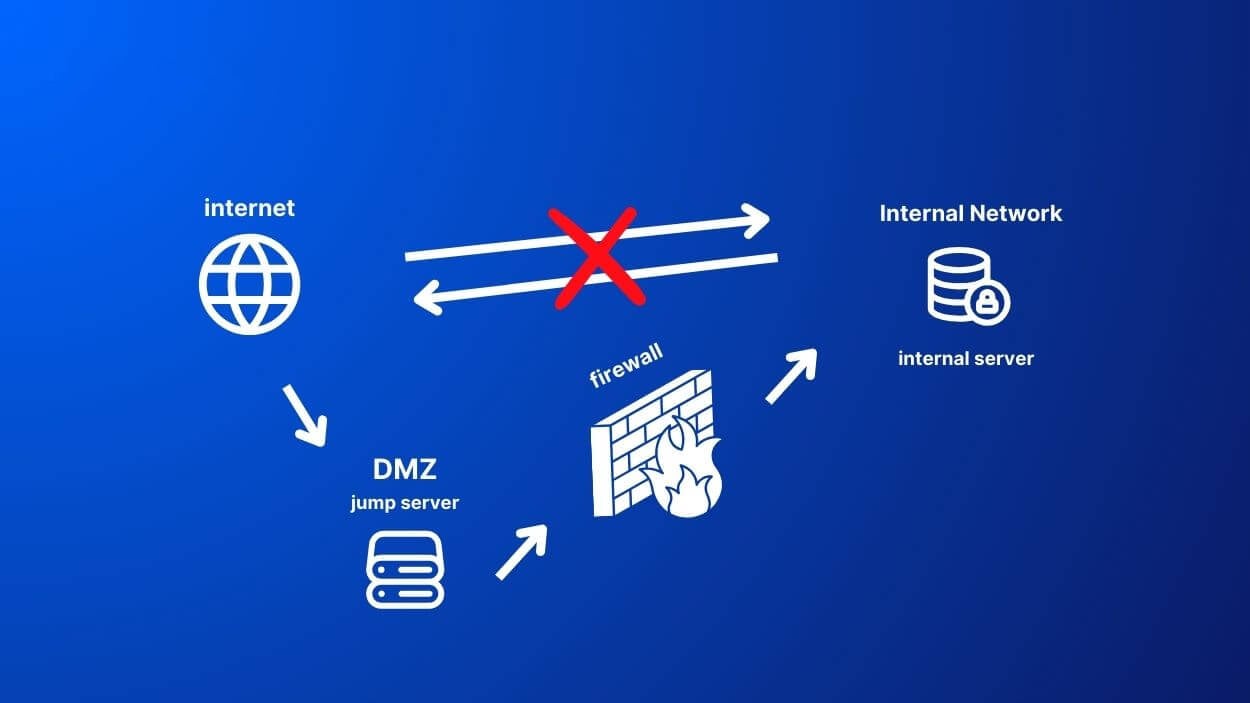
How does it work?
A jump server acts like a security gatekeeper between the internet and a more protected internal network. It’s the first stop for anyone trying to access an internal network from outside.
Before accessing a network in a different security zone, the user must authenticate. Best practices require using multi-factor authentication. After that, the user can connect to internal resources, while the jump server keeps a close watch. One of its functions is to log all activity. The jump server also enforces tight security rules to restrict what users can do and see.
This configuration helps keep the internal network safe from external threats by controlling access and monitoring interactions. Think of a jump server like the bouncer at the door. It checks IDs and keeps an eye on things to make sure everything inside stays secure.
Benefits of a Jump Server
Jump servers provide a range of benefits that are particularly valuable in securing IT environments and simplifying network management. Here are some of the key advantages:
- Enhanced Security: Jump servers ensure all traffic to internal networks goes through a monitored and controlled single access point. That limits the attack surface by preventing direct access to the network from less secure external networks.
- Centralized Access Control: By funneling all remote access through a jump server, organizations can more effectively manage and monitor who accesses their network and what they access. This centralized approach simplifies the enforcement of access policies and improves compliance with security protocols.
- Audit and Monitoring: With all traffic passing through a single point, jump servers facilitate detailed logging of access and activities. This data is crucial for audit trails, which can help in detecting, investigating, and responding to potential security incidents.
- Reduced Complexity: They can lower the complexity of network configurations by minimizing the number of direct connections allowed across the network. That simplification can reduce overhead in managing network security settings and user permissions.
Cons of using Jump Servers
Having a single access point limits any other avenues hackers can take to infiltrate a demilitarized zone — but it can also make it easier. All it takes is just one user’s credentials to gain unlimited access to an organization’s entire infrastructure. The same goes for VNC jump servers, where an ill-intentioned actor could gain complete control of a device to do whatever they please.
Jump servers also require coding expertise to configure and set up, making it difficult for those unfamiliar with script writing to install the appropriate safety precautions. This can ultimately lead to human error and vulnerabilities that cybercriminals can harness.
Jump servers should also not be relied on for complete security as they only provide front-end security, much like a firewall. Once a hacker bypasses either barrier, they can peruse an organization’s network and resources as if they were an internal user, essentially rendering the jump server obsolete.

Jump Servers vs. VPNs
While both jump servers and Virtual Private Networks (VPNs) provide remote access to network resources, they serve different purposes. VPNs create a secure tunnel between a user’s device and the network, allowing for remote work as if the user were directly connected to the network. Jump servers, on the other hand, are more about controlling and securing administrative access to servers and infrastructure, with a focus on tasks such as management and configuration.
Jump server use cases
- Security management. It acts as a single point where authentication and access can be controlled, reducing the potential attack surface.
- Administrative access. In a business environment, system administrators or engineers can use it to access servers that are located within a secured network or behind a firewall.
- Audit trails. Since all connections pass through the jump server, it can be set up to log activities. This creates an audit trail of who accessed which systems and when, which can be very useful for tracking and auditing purposes.
Conclusion
Jump servers have long been a fundamental element in the security architecture of networks, acting as a bastion host that fortifies access to sensitive zones. However, as cyber threats become more sophisticated and the perimeter-less network model gains traction, the adaptation of next-generation technologies and methodologies like Zero Trust becomes imperative. Nonetheless, when deployed with stringent security controls and in conjunction with modern security paradigms, jump servers can still play a vital role in securing access to critical infrastructure and data.