Data Security – Why is it important?
Data security refers to the process of protecting data from unauthorized access and data corruption throughout its lifecycle. Data security includes data encryption, hashing, tokenization, and key management practices that protect data across all applications and platforms.
What is Data Security?
Data security is the process of protecting corporate data and preventing data loss through unauthorized access. This includes protecting your data from attacks that can encrypt or destroy data, such as ransomware, as well as attacks that can modify or corrupt your data. Data security also ensures data is available to anyone in the organization who has access to it.
Some industries require a high level of data security to comply with data protection regulations. For example, organizations that process payment card information must use and store payment card data securely, and healthcare organizations in the USA must secure private health information (PHI) in line with the HIPAA standard.
But even if your organization is not subject to a regulation or compliance standard, the survival of a modern business depends on data security, which can impact both the organization’s key assets and private data belonging to its customers.

Why is it Important?
All businesses today deal in data to a degree. From the banking giants dealing in massive volumes of personal and financial data to the one-man business storing the contact details of its customers on a mobile phone, data is at play in companies both large and small.
The primary aim of data security is to protect the data that an organization collects, stores, creates, receives, or transmits. Compliance is also a major consideration. It doesn’t matter which device, technology, or process is used to manage, store or collect data, it must be protected. Data breaches can result in litigation cases and huge fines, not to mention damage to an organization’s reputation. The importance of shielding data from security threats is more important today than it has ever been.
Benefits of Data Security
Loss or unauthorized disclosure of valuable data can be quite costly to an organization. It’s the reason data security is quite useful. For instance:
- Safeguards all valuable information: Sensitive information is never supposed to leak. Whether we are talking about bank customers’ details or a hospital’s patients’ information; these are crucial information that is not meant for every prying eye. Data security keeps all this information exactly where it’s meant to be.
- Important for your reputation: Any organization that can keep secrets also helps to build confidence among all stakeholders including customers, who know that their data is both safe and secure.
- Marketing and competitive edge: Keeping sensitive information from illegal access and disclosure keeps you ahead of your competitors. Preventing any access to your future development or expansion plans is key to maintaining your competitive advantage.
- Saves on development and support costs: The earlier you plug security features into your application, the fewer costs you may incur from any future support and development costs in terms of code modifications.

Different Data Security Technologies
Data security technology comes in many shapes and forms and protects data from a growing number of threats. Many of these threats are from external sources, but organizations should also focus their efforts on safeguarding their data from the inside, too. Ways of securing data include:
- Data encryption: Data encryption applies a code to every individual piece of data and will not grant access to encrypted data without an authorized key being given
- Data masking: Masking specific areas of data can protect it from disclosure to external malicious sources, and also internal personnel who could potentially use the data. For example, the first 12 digits of a credit card number may be masked within a database.
- Data erasure: There are times when data that is no longer active or used needs to be erased from all systems. For example, if a customer has requested for their name to be removed from a mailing list, the details should be deleted permanently.
- Data resilience: By creating backup copies of data, organizations can recover data should it be erased or corrupted accidentally, or stolen during a data breach.
Top Threats to Data Security
When people think about threats to data security, the first thing that often comes to mind is a hacker breaking into your servers. But the reality is, the top threats to data security are often internal and a result of the unsafe behaviors of your employees.
For example, IBM and The Ponemon Institute studied the root causes of data breaches in 2020 and found that the top two causes were compromised credentials (often due to weak passwords) and cloud misconfigurations (leaving sensitive data accessible to the public):
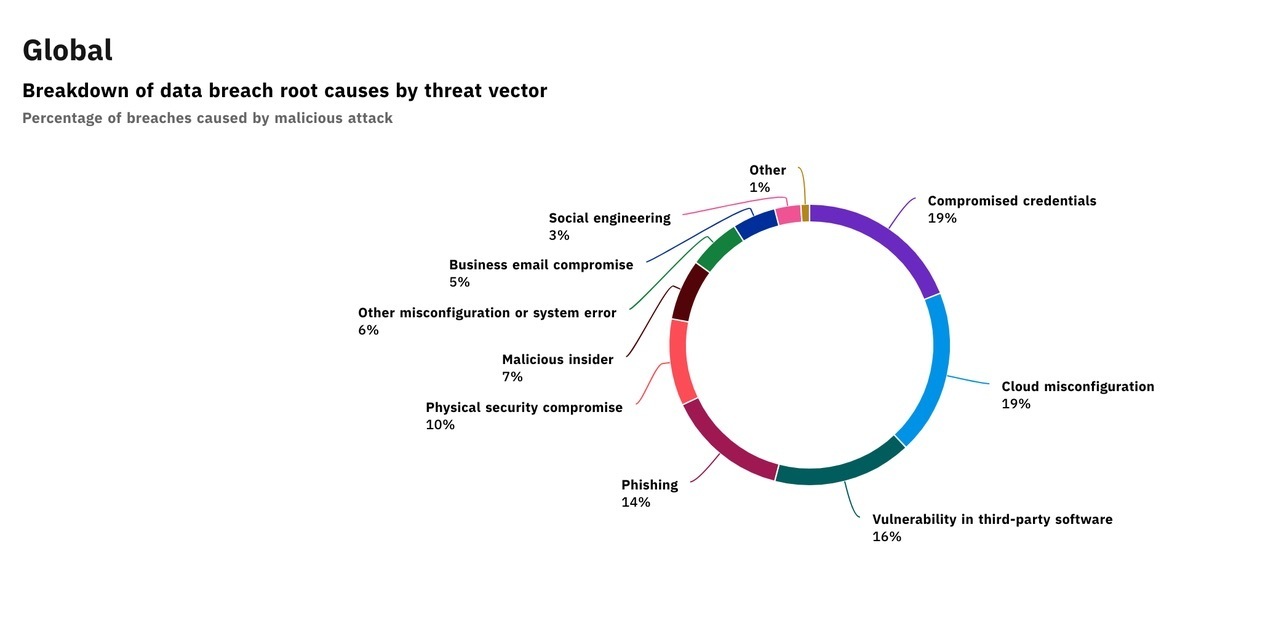
One of the other top causes of data breaches (phishing scams) is also something the right employee training could prevent. IBM’s research shows that teaching employees how to spot phishing emails and other social engineering attacks would help reduce data breaches by 17%.
All that to say, while technologies like firewalls are important for protecting your data against security threats, your teams’ vigilance might be even more so.
Data security trends
- AI: AI amplifies the ability of a data security system because it can process large amounts of data. Cognitive Computing, a subset of AI, performs the same tasks as other AI systems but it does so by simulating human thought processes. In data security, this allows for rapid decision-making in times of critical need.
- Multicloud security: The definition of data security has expanded as cloud capabilities grow. Now organizations need more complex solutions as they seek protection for not only data but applications and proprietary business processes that run across public and private clouds.
- Quantum: A revolutionary technology, quantum promises to upend many traditional technologies exponentially. Encryption algorithms will become much more faceted, increasingly complex, and much more secure.
Conclusion
Developing risk-based data security processes is the key to keeping your data secure. By identifying and classifying your data, understanding and mitigating IT risks, and putting appropriate controls in place, you can strengthen both data security and compliance.