What is a Network Socket?
When it comes to understanding the inner workings of the Internet and computer networks, network sockets play a critical role. If you’re curious about network sockets, how they function, and why they’re essential, this article will guide you through the fundamentals and beyond.
What is a Network Socket?
A network socket is a software abstraction that allows computers to communicate with each other over a network. It is an endpoint for sending and receiving data, enabling devices to exchange information seamlessly. Think of a socket as a virtual bridge that connects two systems, whether on a local network or across the globe via the internet.
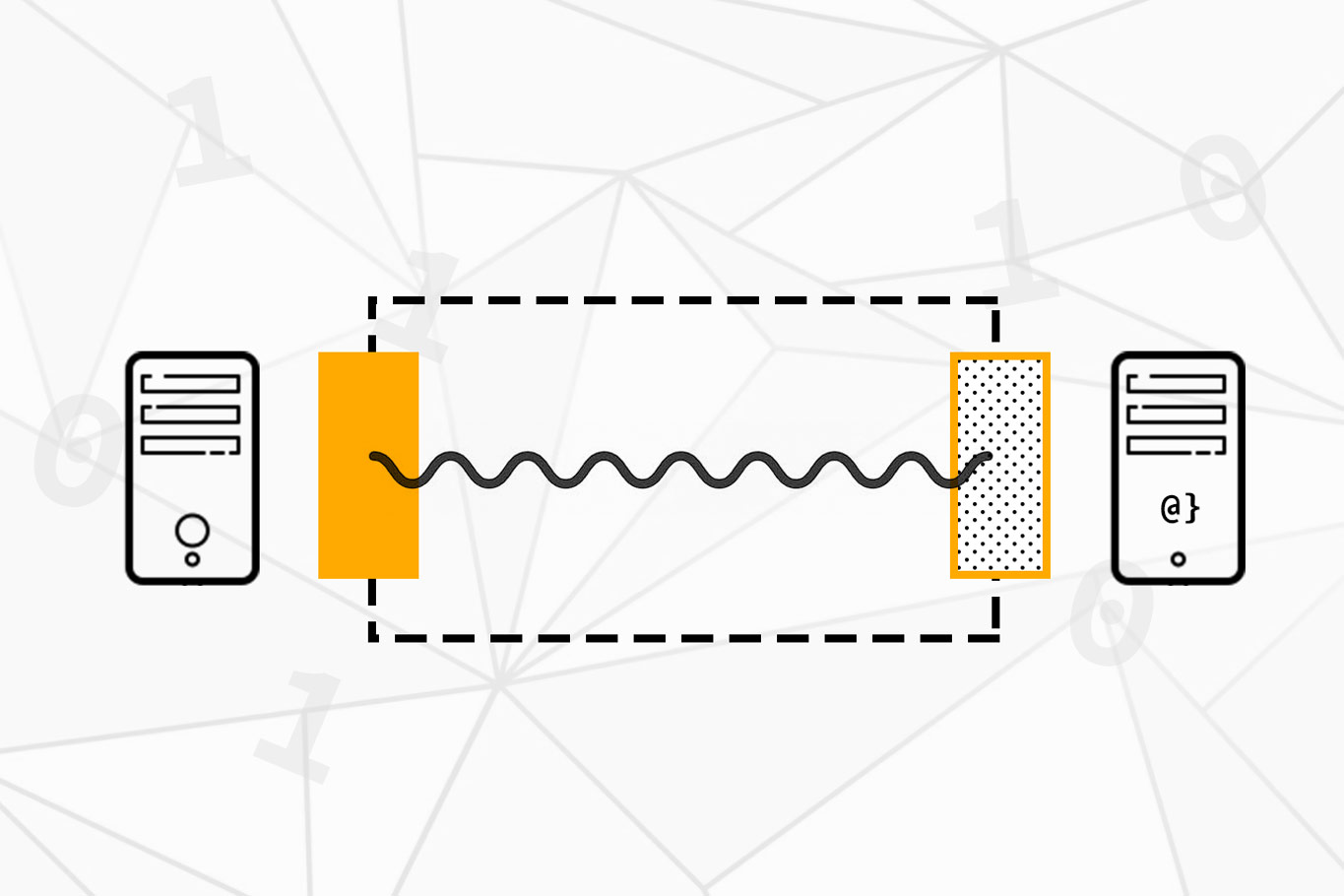
How Do Network Sockets Work?
Network sockets operate using the Internet Protocol (IP) suite, primarily relying on two key protocols:
Transmission Control Protocol (TCP)
- Ensures reliable, ordered, and error-checked delivery of data.
- Commonly used for applications requiring high reliability, such as web browsing and email.
- Focuses on speed and efficiency, without guaranteeing delivery.
- Ideal for applications like online gaming, video streaming, and voice calls.
Each socket is identified by a unique combination of three elements:
- IP Address: Identifies the host device on the network.
- Port Number: Specifies the application or service.
- Protocol: Defines the communication rules (TCP or UDP).
Types of Network Sockets
Stream Sockets (TCP Sockets)
- Provide a continuous stream of data.
- Ensure error correction and retransmission.
- Ideal for scenarios requiring reliable communication, such as file transfers and web browsing.
Datagram Sockets (UDP Sockets)
- Handle discrete chunks of data, known as datagrams.
- Do not guarantee delivery or order.
- Suitable for applications where speed is more critical than reliability.
Raw Sockets
- Provide access to lower-level protocols, allowing custom packet creation.
- Typically used by network diagnostic tools and advanced applications.
Common Uses
Network sockets are fundamental to various applications, including:
- Web Browsing: Browsers use sockets to connect to web servers and retrieve content.
- Email Communication: Email clients and servers exchange messages via sockets.
- Online Gaming: Multiplayer games rely on sockets for real-time data exchange.
- Streaming Services: Audio and video streaming platforms use sockets for smooth playback.
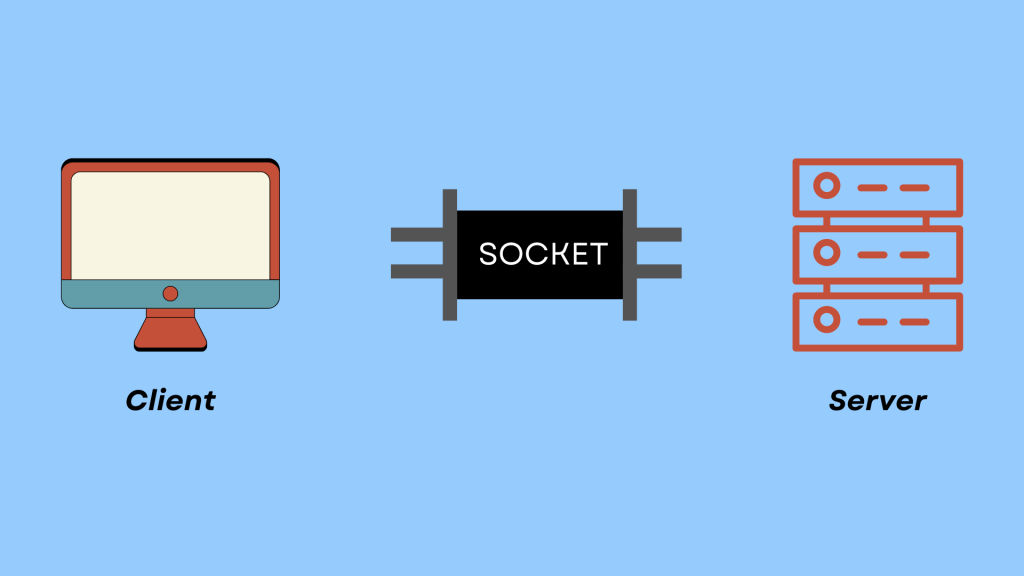
Security Considerations for Network Sockets
While network sockets are essential, they can also be a vector for security threats if not managed properly. Here are some best practices:
- Use Secure Protocols: Opt for encrypted communication protocols like HTTPS and TLS.
- Validate Input: Prevent injection attacks by sanitizing data sent through sockets.
- Implement Firewalls: Restrict unauthorized access to sensitive ports.
- Monitor Traffic: Use tools to detect and mitigate suspicious activity.
Conclusion
Network sockets are the backbone of modern communication, enabling devices to connect and exchange data efficiently. Whether you’re a developer, network engineer, or tech enthusiast, understanding how sockets work is crucial for navigating the digital world. By mastering the fundamentals of network sockets, you’ll gain valuable insights into the technologies that power our interconnected world.