What is Internet Control Message Protocol (ICMP)?
Internet Control Message Protocol (ICMP) is a communication system with many functions. Your system is prepared to send data to another system. Will the messages go through properly? Or is something blocking clear and crisp communication? Devices use the ICMP to share status information just like this. The protocol could be critical if your network encounters a communication problem, and you need to diagnose it quickly.
Every day, the average employee wastes 22 minutes on IT issues. If you’re running the network, keeping things running smoothly is critical. ICMP can help you do just that. But ICMP does have a dark side. Sometimes, hackers use it to flood your server with so many requests that you lose connectivity altogether.
What is Internet Control Message Protocol?
The Internet Control Message Protocol, which is most known by its friendlier acronym ICMP, is a protocol that’s fundamental to troubleshooting various connectivity-related issues.
This protocol is used by a wide variety of network devices, including but not limited to routers, modems, and servers to inform other network participants about potential connectivity issues.
We’ve mentioned above that ICMP is a protocol just like Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), but unlike those two, ICMP is not generally used to facilitate the exchange of data between systems. Furthermore, it’s not frequently used in end-user network apps, unless they’re diagnostic tools.
ICMP’s original definition was sketched by Jon Postel, who contributed massively and many times to the development of the Internet, and the first standard of ICMP was published in April 1981 in RFC 777.
The initial definition went through a lot of changes to reach the form that we’re familiar with today. The stable form of this protocol was published 5 months later than its initial definition, in September 1981, in RFC 792, and was also written by Postel.
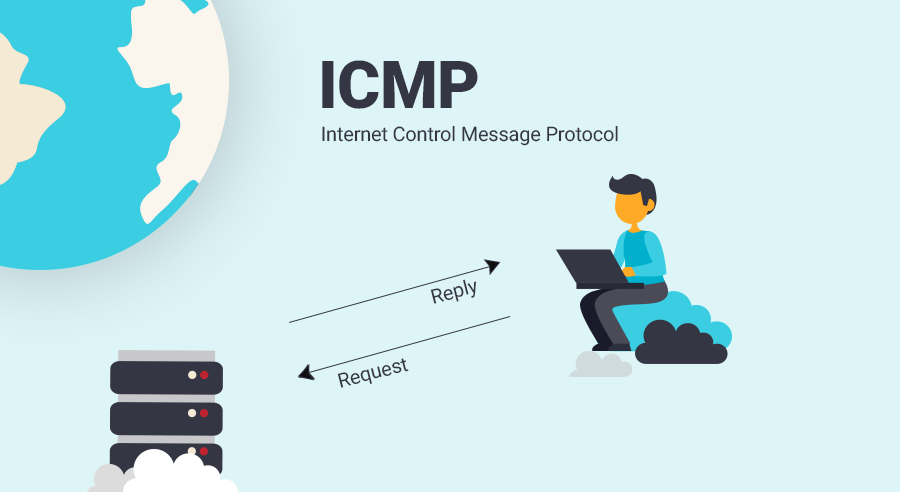
What is Internet Control Message Protocol used for?
The primary purpose of ICMP is for error reporting. When two devices connect over the Internet, the ICMP generates errors to share with the sending device if any of the data does not get to its intended destination. For example, if a packet of data is too large for a router, the router will drop the packet and send an ICMP message back to the source of the data.
The secondary use of ICMP protocol is to perform network diagnostics; the commonly used terminal utilities traceroute and ping both operate using ICMP. The traceroute utility is used to display the routing path between two Internet devices. The routing path is the actual physical path of connected routers that a request must pass through before it reaches its destination. The journey between one router and another is known as a ‘hop,’ and a traceroute also reports the time required for each hop along the way. This can be useful for determining sources of network delay.
The ping utility is a simplified version of the traceroute. Ping will test the speed of the connection between two devices and report exactly how long it takes a packet of data to reach its destination and come back to the sender’s device. Although ping does not provide data about routing or hops, it is still a very useful metric for gauging the latency between two devices. The ICMP echo-request and echo-reply messages are commonly used to perform a ping.
Unfortunately, network attacks can exploit this process, creating means of disruption such as the ICMP flood attack and the ping of death attack.
How Does ICMP Work?
ICMP differs from Internet Protocol (IP) version 6 or IPv6 in that it is not associated with TCP or UDP. As a result, there is no need for a device to connect with another before sending an ICMP message.
For example, in TCP, the two devices that are communicating first engage in a handshake that takes several steps. After the handshake has been completed, the data can be transferred from the sender to the receiver. This information can be observed using a tool like TCPDUMP.
ICMP is different. No connection is formed. The message is simply sent. Also, unlike TCP and UDP, which dictate the ports to which information is sent, there is nothing in the ICMP message that directs it to a certain port on the device that will receive it.
Internet Control Message Protocol in DDoS attacks
In distributed DoS (DDoS) attacks, attackers overwhelm the target with unwanted traffic so the target cannot provide service to its users. There are multiple ways an attacker can use ICMP to execute these attacks, including the following:
- Ping of death: The attacker sends an IP packet larger than the number of bytes allowed by IP. On the way to its intended destination, the oversized packet is fragmented. However, when the recipient device reassembles it, the size exceeds the limit, causing a buffer overflow and the receiving machine to freeze or crash. Newer devices have defenses against this older-type attack, but legacy networking devices are still vulnerable to it.
- ICMP flood attack: Sometimes called a ping flood attack, the goal of this attack is to overwhelm the target device with echo request packets. Each echo-request packet must be processed by the target and responded to with echo reply messages. This sucks up all the target computer’s resources, and it causes a denial of service to any other users of the target computer.
- Smurf attack: In a Smurf attack, the attacker sends an ICMP packet with a spoofed source IP address, and the network layer equipment replies to the packet, sending the spoofed address a flood of packets. Like the ping of death, Smurf attacks are more likely to work on undefended legacy equipment.

Conclusion
All things considered, although ICMP isn’t used to exchange information between connected devices on a given network as TCP and UDP do, it still has a huge applicability range. In fact, ICMP is one of the most flexible fundamental protocols that help keep the Internet the way we know it.
Aside from its basic purpose of letting one system know when there’s a choke in its connection to another system, ICMP is the backbone of numerous troubleshooting tools such as ping, pathping, and traceroute. Unfortunately, it also helps malicious agents deliver a wide range of DoS and infiltration attacks to vulnerable machines.