Network Perimeter: Why is it important?
Securing a company-wide network is imperative for any organization. Hackers have more opportunities than ever to break through network perimeters and steal valuable information. The reality is that the perimeter is vanishing due to continued expansion for organizations of all sizes. Companies need to protect themselves from hackers who can strike from anywhere in the world.
What is a Network Perimeter?
The network perimeter is the boundary between an organization’s secured internal network and the Internet — or any other uncontrolled external network. In other words, the network perimeter is the edge of what an organization has control over.
Suppose an office has an internal network to which a rack of servers, several dozen employee desktop computers, a few printers, and networking equipment such as routers and switches are connected. If an employee brings their personal laptop into the office, the laptop is outside the network perimeter — unless they can connect it to the network.
Why is it important?
The increasing reliance on an interconnected ecosystem of online devices in today’s business environment has greatly increased our reliance on network protection to prevent cyber attacks. Data is collected, collated, and interpreted on a massive scale, and its security is dependent on the protections that surround it. The concept and evolution of a network perimeter allow organizations to think effectively about how to safeguard their internal information from untrusted or malicious actors.
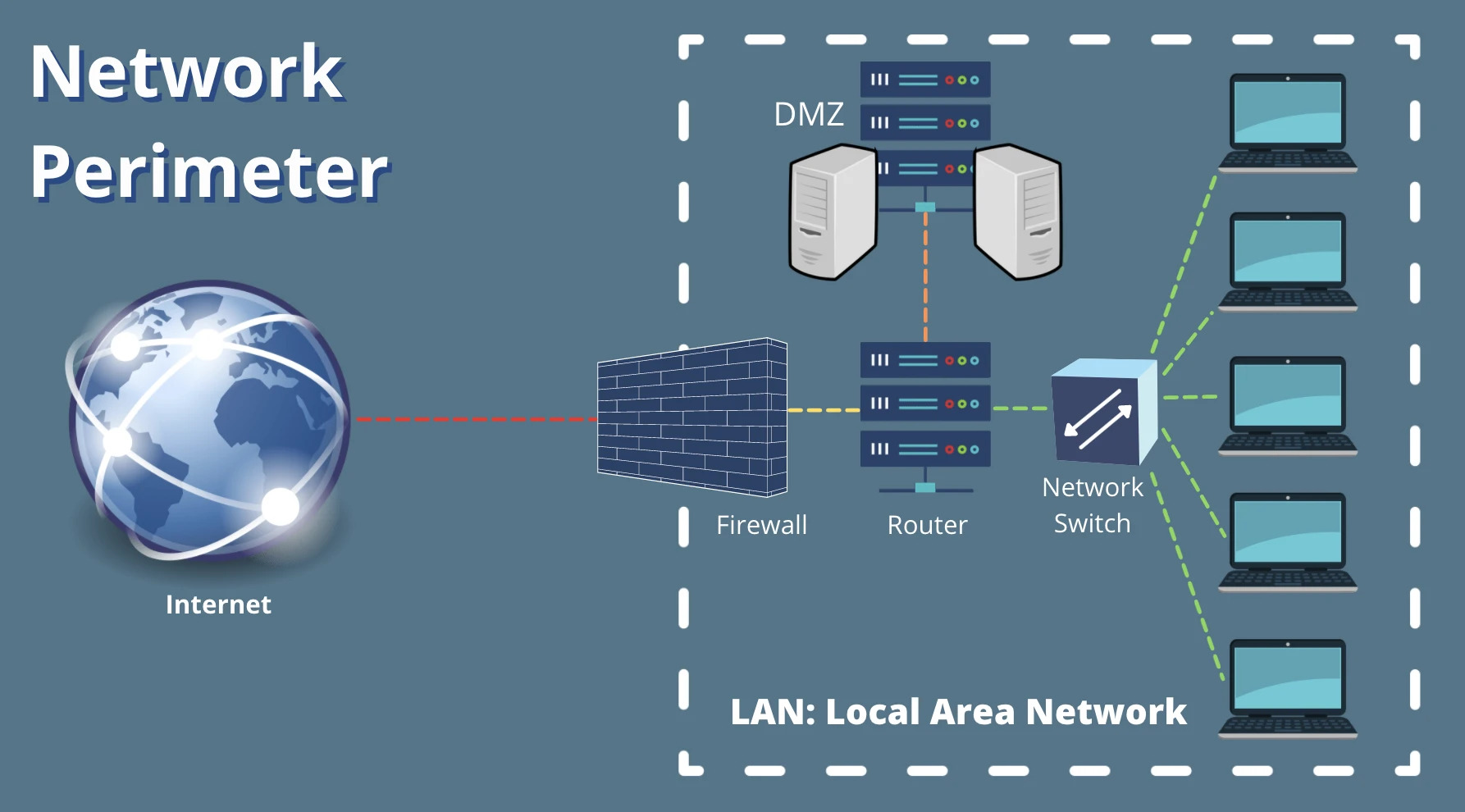
Components of a Network Perimeter
- Border Routers: Routers serve as the traffic signs of networks. They direct traffic into, out of, and throughout networks. The border router is the final router under the control of an organization before traffic appears on an untrusted network, such as the Internet.
- Firewalls: A firewall is a device that has a set of rules specifying what traffic it will allow or deny to pass through it. A firewall typically picks up where the border router leaves off and makes a much more thorough pass at filtering traffic.
- Intrusion Detection System (IDS): This functions as an alarm system for your network that is used to detect and alert suspicious activity. This system can be built from a single device or a collection of sensors placed at strategic points in a network.
- Intrusion Prevention System (IPS): Compared to a traditional IDS which simply notifies administrators of possible threats, an IPS can attempt to automatically defend the target without the administrator’s direct intervention.
- De-Militarized Zones / Screened Subnets: DMZ and screened subnets refer to small networks containing public services connected directly to and offered protection by the firewall or other filtering device.
When do you need a Network Perimeter?
Not every business needs a network perimeter. Small businesses might not need a perimeter, but the introduction of an at-home workforce requires infrastructure to protect data when employees connect from external sources. Compliance regulations require certain safeguards for remote user access, but every business should design infrastructure that builds cyber security into network connectivity.
A few scenarios where you should build a network perimeter:
- Remote workers connect to internal resources using a VPN
- Public services are hosted on-premises, and users are given access to them from the internet
- Internal applications hosted in the cloud and accessible to at-home employees
- API applications allow the public to query data from the internet
- Any assets that must be available on the internet and hosted on-premises
Many businesses have a hybrid cloud environment, which means that they host some corporate resources on-premises, and other resources are hosted in the cloud. Connectivity between these two environments is controlled using cloud services including Identity and Access Management (IAM). Firewalls, IPS, and IDS protect both the cloud and local network and monitor the environment for any suspicious activity.

Conclusion
The network perimeter may continue to expand, which makes protecting the perimeter network even more difficult. Organizations should keep up to date on the latest cyber security trends to ensure the continued protection of the network perimeter.