What is a Reverse Proxy?
As an online business, you have a lot expected of you. Your website must be consistently fast, secure, and reliable enough to keep visitors coming back. Anything less and you risk looking unprofessional to prospective customers. There is a wealth of technologies to make the process of building and maintaining a website as hands-off as possible: content management systems to publish your site’s content, full-service hosting providers that give your site a home, and even website builders that can handle almost every aspect of your site. In this post, we’re going to explore another common method leveraged by businesses to run safe, high-performing websites – it’s called a reverse proxy. That term might sound a bit cryptic now, but the concept of a reverse proxy and its uses is relatively straightforward if you understand the basics of the internet.
What is a Reverse Proxy?
A reverse proxy is a proxy server that acts as a gateway to a web server. When you send requests to a web server that makes use of it, your requests do not go to the web server; they will go to the reverse proxy which will then determine if it should route it to the web server or block it.
This means that with a reverse proxy in place, you never get to have direct communication with the web server using it. You wouldn’t even though that it is there as it will appear to you like the actual server. See them as some kind of wrapper around a web server or a cluster of servers. They can protect it against attacks and provide better web performance by way of load balancing and caching.
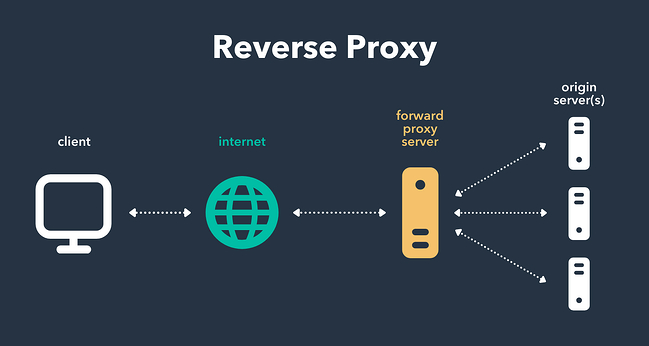
How does it work?
A reverse proxy gets in the flow of traffic and secures access to sanctioned cloud resources by integrating with said resources as well as an organization’s identity provider (IDP) via SAML (which stands for Security Assertion Markup Language and is used for exchanging authorization and authentication data between users and cloud services). Through this integration, which entails configuring cloud apps’ single sign-on (SSO) settings to point to it, the CASB can operate in line without the need for agents.
In the user experience, when someone signs into an SSO service to access managed cloud apps, that user’s traffic is automatically redirected to the reverse proxy, which operates in the data path and serves as a middleman. It plays the role of the user for the cloud app, and the cloud app for the user, passing information back and forth while applying real-time security policies.
Benefits
Load Balancing
Reverse proxies can decide where and how they route Hypertext Transfer Protocol (HTTP) sessions. In this way, it can be used to distribute the load in a manner that maximizes the experience of the end-user. Load balancing also produces a more efficient, useful network. It can prevent servers from getting overworked, thereby limiting the number of bottlenecks the site experiences and ensuring smoother operation.
This may be particularly helpful during busier times of the year when a large number of HTTP sessions attempt to interact with your origin server all at the same time. As the reverse proxy balances the load of the work that has to be performed, it eases the burden on your network.
Protection from attacks
With a reverse proxy in place, a website or service never needs to reveal the IP address of its origin server(s). This makes it much harder for attackers to leverage a targeted attack against them, such as a DDoS attack.
Global Server Load Balancing (GSLB)
Global server load balancing (GSLB) is load balancing that is distributed around the world by way of a reverse proxy. With GSLB, the requests going to a website can be distributed using the geographic locations of the clients trying to access it. As a result, requests do not have to travel as far. For the end-user, this means the content they have requested can load faster.
Caching
A reverse proxy can also cache content, resulting in faster performance. For example, if a user in Paris visits a reverse-proxied website with web servers in Los Angeles, the user might connect to a local reverse proxy server in Paris, which will then have to communicate with an origin server in L.A. The proxy server can then cache (or temporarily save) the response data. Subsequent Parisian users who browse the site will then get the locally cached version from the Parisian reverse proxy server, resulting in much faster performance.
SSL Encryption
Secure socket layer (SSL) encryption can be a costly endeavor, particularly because there are so many communications that need to be encrypted and decrypted as they stream in from various clients. However, with a reverse proxy, all SSL encryption can happen on the reverse proxy itself.

How to implement a Reverse Proxy?
Implementing a reverse proxy begins with figuring out what you want it to do. You will want to write down your hopes for the reverse proxy before contacting a service provider. Then, you will want to make sure your site and the reverse proxy are both hosted by a single provider. The next step is to reach out to your provider and present what you want it to do.
Because an HTTP reverse proxy can be used for several different things, you will want to be specific regarding your goals. Your provider will then take the objectives you presented and use them to configure your reverse proxy. This is accomplished through the design and implementation of rules. Each rule tells the reverse proxy what to do, when, and in the context of specific situations.
Conclusion
Reverse proxies have their usefulness in the request and response cycle. While they can be used for security, they also can give end-users more responsive responses in the case of high-traffic websites. They are usually transparent and you wouldn’t even know they are there since some hide the footprint you can use to know of their presence.